I came across an unusual DHL branded phish recently…
The user receives an email with the Subject of “DHL delivery to [ xxx ]June ©2015” where xxx is their valid email address. The From is forged as “DHLexpress<noreply@delivery.net>” (the criminal will have used this domain since delivery.net hasn’t yet adopted DMARC whereas dhl.com has a p=reject policy which would have prevented this type of forgery altogether).
The email looks like this (I’ve blacked out the valid email address):
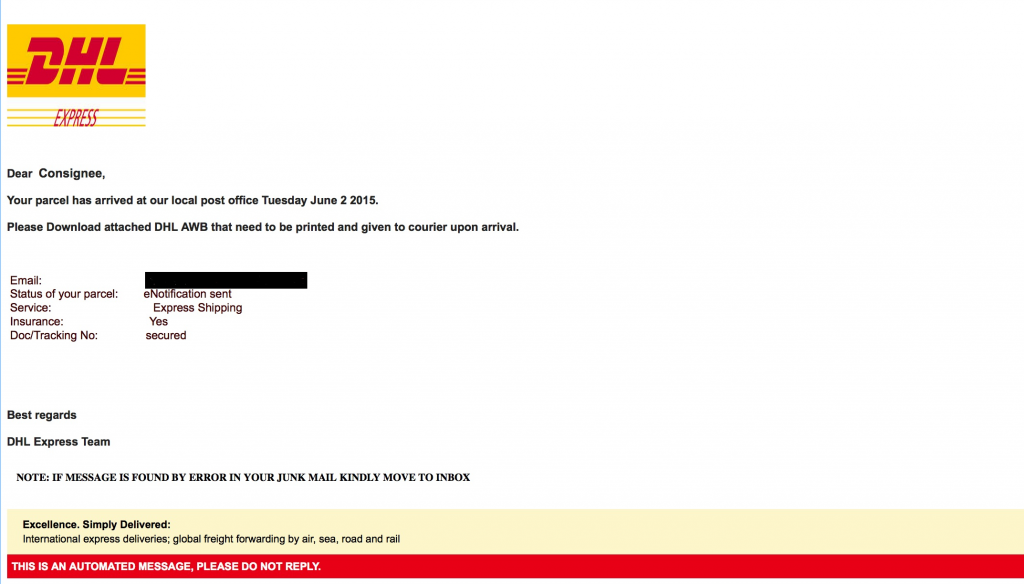
and so, although we would all wish otherwise, it is predictable that many recipients will have opened the attachment.
BTW: if the image looks in the least bit fuzzy in your browser then click on the image to see the full-size PNG file and appreciate how realistic the email looks.
I expect many now expect me to explain about some complex 0-day within the PDF that infects the machine with malware, because after all, that’s the main risk from opening unexpected attachments isn’t it ?
But no!
Continue reading Phishing that looks like another risk altogether